It took a while, but here is a report of the last KoC trip to Oaxaca, Mexico. Recently, some of us have been very busy due to exciting professional changes, but it is important to let people know that we continue working towards bringing Free Open Source Software, Computers and Education to underprivileged communities in diverse areas.
After having a blast at the last Southern California Linux Expo the Kids on Computers crew traveled to Oaxaca, Mexico with the mission of setting up two new labs, which had been previously approved by the board of directors.

Before going into details about the trip, I have to say that many people are involved in the planning process of every KoC trip and, due to a number of reasons, many of them are not able to get on a plane and visit the schools and meet the communities that benefits from their hard work. I want to express my gratitude and appreciation to all of them.
So this time was very special. We had plans to set up two new labs near Oaxaca city as well as visiting most of the labs we have in both the Huajuapan and Monte Albán area (this area in particular is 20 minutes from downtown Oaxaca). All this within a week and with less than 10 volunteers, actually we were only 8 this time. So in order to accomplish this mission we had to come up with a different plan compared to other years. We split into two groups, the Laptop (LPT) team, who was in charge of setting up a lab in the Antequera School and the Raspberry Pi (RPI) team, who was in charge of setting up the lab in Constitución de 1917 school. Yeah, we set up our second Raspberry Pi lab in Oaxaca! (you can learn more about the first one here 🙂 )
Below you can see the people in each group and our schedule:
Group LPT (OAX / Huajuapan)
- George
- Avni
- Hermes
- Thomas
- Adam (Thurs-Friday)
Group RPI (OAX)
- Gustavo
- Tim
- Peter (Mon-Tues)
- Adam (Mon-Wed)
Monday (Apr 24) – Day 1
-
Group LPT – OAX
-
Group RPI – OAX
Tuesday (Apr 25) –
Wednesday (Apr 26) –
Thursdays (Apr 27) –
-
Group LPT – Huajuapan
-
Group RPI – OAX
Friday (Apr 28) –
-
Group LPT – OAX
-
Group RPI – OAX
César, one of the volunteers that could not join us in this trip, prepared Ubermix 3 for the Laptops and Raspbian for the Pi’s prior to the trip. It worked very well. Ubermix 3 was much more responsive than Ubermix 2 on older laptops.
Some microSD card issues
We ran into some problems with one type of microSD card we wanted to use for the Pi’s. It turned out that some 16GB microSD cards don’t have enough space for the Raspbian distro that César prepared.

Tim and I ended up walking all around Oaxaca city, trying to find the right one to use.

Below you can see some photos we took in Tim’s room at hotel Aurora in downtown Oaxaca, while we were trying out different microSD cards.



Until we found it!
The RPI servers Adam, Tim and George prepared prior to the trip worked out of the box!


The Antequera School
The LPT team did a remarkable job getting rid of Windows and installing Ubermix 3 on 13 desktops in Antequera school. This lab was already operational but they wanted some extra computers. So we gave them some laptops, cast a spell and turned the whole lab to the Open Source. 😀



The kids learned the importance of testing. 😛
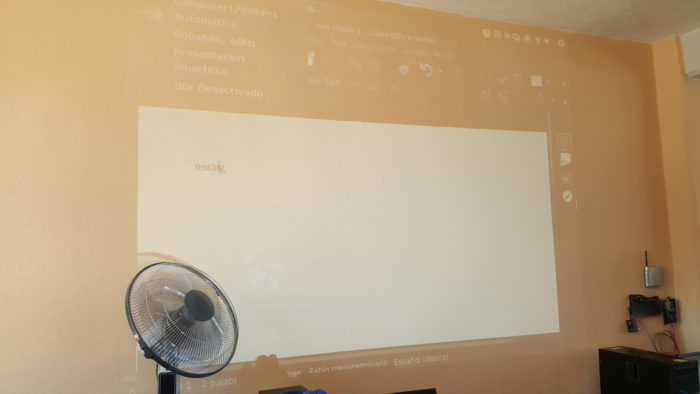
Internet in a Box working just fine:


Constitución de 1917 school
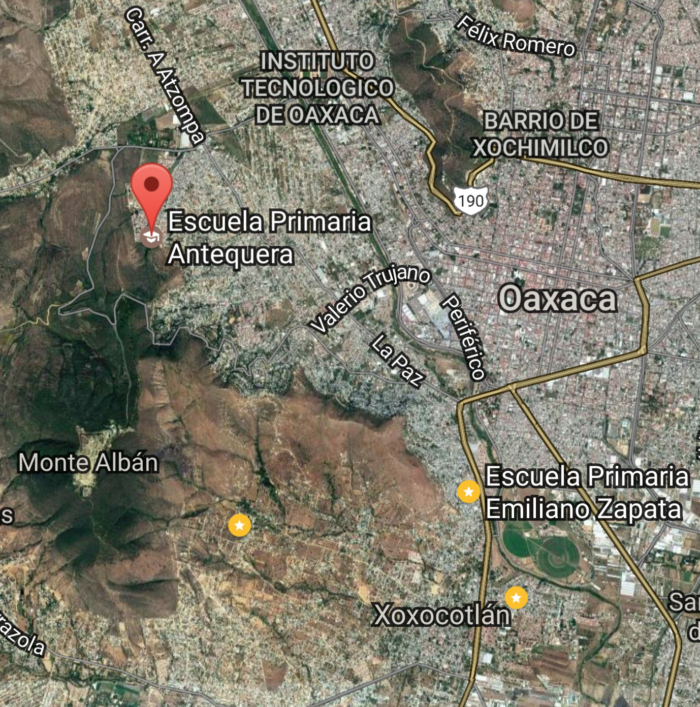
This school is located in San Javier, Xoxocotlán, Oaxaca. The map below gives you an idea of the distance between our first Raspberry Pi lab and this new one. They are actually pretty close and, we consider this a great advantage for both the communities to interact and support each other and for us, once we don’t have to travel long distances to visiting the labs when we are in town. You also can see two stars on your right side of the map. Those are two more KoC labs. The one on the top is Emiliano Zapata elementary school (our first lab in the Monte Albán area, near Oaxaca city) and the one on the bottom is Benito Juárez.
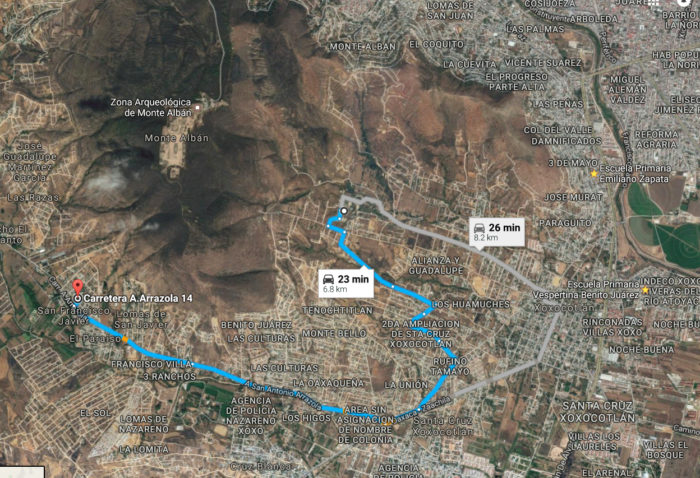
Follow this link to interact with the map and get familiar with the neighborhood.

We found out this school has a very nice library:




Juan Villoro is my favorite Mexican writer and, in my opinion, one of the best ones. El libro salvaje (The wild book) is a story about a book that doesn’t want to be read, which is a pretty clever way of tricking kids into reading. I was very happy and amazed to find this book in the school library.

This lab was a little bit challenging to set up. First, as I wrote above, we had to find the right microSD cards to use, then we had some problems with the resolution of the monitors, so we had to reconfigure the Pi’s manually.
We bought the monitors locally and, it turned out that some of the mounting screws were not the proper ones. The school personnel was very supportive and one of them went all the way down to downtown Oaxaca and got us the right ones. Below you can see Peter working on the monitors.

Then we had to figure out how to hook the Pi’s to the monitors.




As you can see below, at the end everything worked out fine thanks to a very determined group of volunteers. We made our way out of the school around 10PM walking in heavy rain, but with the priceless satisfaction of having set up a very nice and completely functional Raspberry Pi lab (with Pi’s 3) with Internet in a Box running on a Raspberry Pi 3, plus a projector.



In a future post I will write about our visits to some of the other labs we have in Oaxaca. It’s been very exciting to write this post and recall the things we experienced and went through during that week.
The prequel – Two days before Day 1
Special kudos go to Adam, who on his arrival at Mexico city spent the whole day at the Technology Plaza purchasing projectors, keyboards, mice, headphones and regulators. He compared prices looking for the best deals, trying to make the most out of our funds and, searched the whole plaza for Raspberry Pi cases. Adam ended up carrying 11 bags to the bus station between purchased equipment and peripherals he was already carrying with him. He left Mexico city and arrived in Oaxaca city at 2:30AM the next day. Thomas, Peter and Avni picked him up in 2 taxis.
It would have been very complicated if not impossible to set up our 2 new labs without Adam’s great spirit and remarkable work. Thank you, Adam!

Some words on the trip by KoC President Avni Khatri:
“To say the least, our KOC trips are never without an adventure – there are so many lessons learned on this trip. Many thanks to everyone here and at home for your hard work and dedication. It is very much appreciated and is allowing us to achieve our goal to provide access to technology to kids in underserved areas.”
Thank you to everyone who contributed to make this trip a success. We want to go back to Mexico this November, so stay tuned if you want to join us.
We are currently raising funds for two new labs. Please help us make it a reality by donating here. Every little bit helps! 🙂